

PCI Security standard for every Entity that store, process or transmit cardholder data and/or sensitive authentication data. We provide full range of services including initial gap-assessment, remediation support, penetration testing, ASV scans and final (annual) audit.
Our flexible approach means we can tailor our PCI DSS service specifically to your requirements and budget. The exercise consist of all the core areas that needs to be taken care off in understanding the environment and making it compliant and ensuring its compliance to the next level i.e. maintaining certification. A detailed Gap Analysis that includes full PCI DSS Discovery and Scoping with a view to reducing the overall cost of compliance.
![]() A definition of your Cardholder Data Environment (CDE).
A definition of your Cardholder Data Environment (CDE).
![]() Mappings of in-scope business processes, applications, devices, networks, facilities and service providers – all the information you need to fully define the scope and boundaries of your CDE.
Mappings of in-scope business processes, applications, devices, networks, facilities and service providers – all the information you need to fully define the scope and boundaries of your CDE.
![]() An assessment of each of the PCI DSS requirements applicable to your organization.
An assessment of each of the PCI DSS requirements applicable to your organization.
![]()
Compliance scores that show your organization’s compliance ratings against PCI DSS as a whole, each of the 12 PCI DSS requirements, as well as the 6 milestones of the PCI DSS Prioritize Approach.
![]() Detailed recommendations for each non-compliant PCI DSS requirement.
Detailed recommendations for each non-compliant PCI DSS requirement.
![]() Recommendations for reducing the scope of the CDE, where applicable, thus reducing the potential cost of compliance.
Recommendations for reducing the scope of the CDE, where applicable, thus reducing the potential cost of compliance.
![]() Advice regarding your organization’s best options for achieving PCI DSS compliance quickly and cost-effectively, drawing upon our QSA’s experience working with similar organizations.
Advice regarding your organization’s best options for achieving PCI DSS compliance quickly and cost-effectively, drawing upon our QSA’s experience working with similar organizations.


The Payment Card Industry Security Standards Council maintains the PA-DSS, which it published in 2008 as a replacement for Visa’s Payment Application Best Practices (PABP) standard.
To achieve PA-DSS compliance, a software provider must have its applications audited by a Payment Application Qualified Security Assessor (PA-QSA) and revalidated whenever any major changes are made.
Compliance Wing’s PA-QSA’s assist you in adhering to The PCI Payment Application Data Security Standard (PA-DSS) requirements and Security Assessment Procedures define security requirements and assessment procedures for software vendors of payment applications.
PA-DSS is a set of requirements that are intended to ensure software suppliers develop secure payment applications that support PCI DSS compliance. PA-DSS applies to third party applications that store, process or transmit payment cardholder data as part of an authorization or settlement. Software applications that are developed for the use of one merchant only are exempt from PA-DSS but must comply with PCI DSS.


Compliance with the ISO 27001:2013/2022 Information Security Management Systems standard ensures that you have taken the correct steps to ensure the integrity of your data and systems, so that they are protected from security threats. Compliance Wing can help you achieve ISO 27001:2013 certification. With the increase in opportunities to do business globally and the increased flow of information combined with the increase in sophistication of information security attacks, there is an urgent need to protect the confidentiality, integrity and availability of information. An ISO 27001 gap analysis is often the recommended place to start an ISO 27001 compliance project. Our expert-led gap analysis includes interviews with key staff and a review of your existing information security plans and documentation.

SOC 1 focuses on controls relevant to financial reporting, ensuring that service providers meet industry standards for security and compliance. It is particularly crucial for organizations that process financial data, as it helps maintain integrity, reliability, and regulatory adherence. A SOC 1 audit, conducted under SSAE 18, assesses internal controls over financial reporting (ICFR), ensuring transparency and reducing financial risk.
SOC 2 compliance is designed for technology and cloud-based service providers, evaluating controls related to security, availability, processing integrity, confidentiality, and privacy. Organizations undergo rigorous audits to demonstrate adherence to the Trust Services Criteria (TSC), ensuring robust security measures, continuous monitoring, and data protection. Achieving SOC 2 certification.
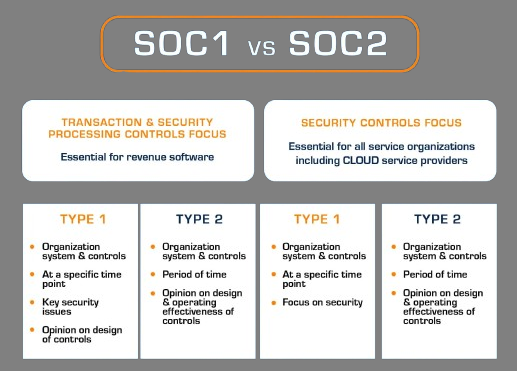
The primary difference between a SOC 1 and SOC 2 report is in the scope: A SOC 1 report is concerned with the implementation of financial controls, whereas SOC 2 attestation reports focus more extensively on availability, security, processing integrity, confidentiality, and privacy.
While SOC 2 identifies and tests control that meets the requirements, SOC 1 tests control that adheres to the identified control objectives.
ISO/IEC 27017 is a globally recognized standard that provides comprehensive guidelines for enhancing the security of cloud services. Our company specializes in assisting organizations in achieving compliance with ISO/IEC 27017 requirements. This framework offers tailored security controls and best practices specifically designed for cloud environments, ensuring the confidentiality, integrity, and availability of data stored and processed in the cloud.
By leveraging our expertise, organizations can strengthen their cloud security posture, mitigate risks, and demonstrate commitment to safeguarding sensitive information. Our services empower businesses to navigate the complexities of cloud security compliance effectively, fostering trust among stakeholders and enhancing the overall resilience of their cloud infrastructure.

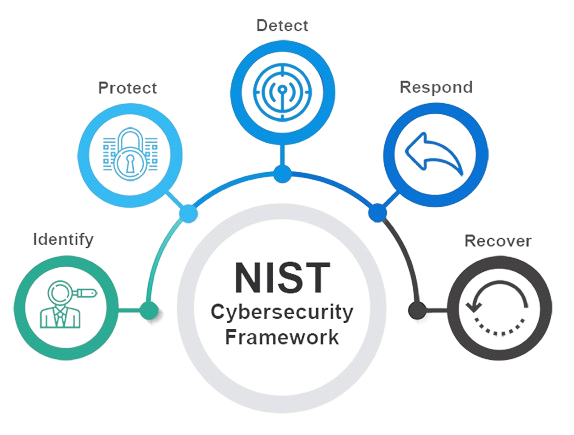
The NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology (NIST), offers a structured approach to managing and enhancing cybersecurity risk management processes. Comprising Core Functions such as Identify, Protect, Detect, Respond, and Recover, this framework provides a comprehensive set of guidelines and best practices.
By breaking down these functions into categories and subcategories, organizations can assess their cybersecurity posture, identify vulnerabilities, and implement targeted improvements. Highly adaptable and scalable, the framework suits organizations of varying sizes and sectors, fostering a common language and structure for cybersecurity resilience. Widely adopted by both public and private entities, the NIST Cybersecurity Framework serves as a valuable resource for bolstering cybersecurity defenses and mitigating risks effectively.
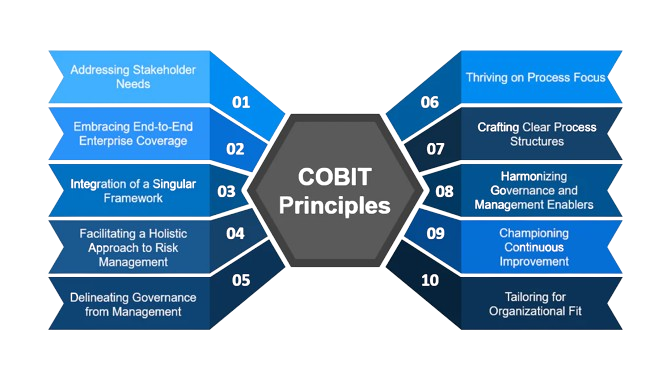
COBIT, or Control Objectives for Information and Related Technologies, is a globally recognized framework designed to help organizations effectively govern and manage their IT environments. Developed by ISACA, COBIT provides a comprehensive set of best practices and guidelines for aligning IT goals with business objectives, managing IT-related risks, and ensuring compliance with regulations and standards.
With COBIT, organizations can establish robust governance structures, define clear roles and responsibilities, and implement effective control mechanisms to optimize the use of IT resources and enhance overall performance. By adopting COBIT, businesses can streamline their IT processes, improve decision-making, and build trust with stakeholders by demonstrating a commitment to sound IT governance practices.
Our company offers expert assistance in implementing COBIT, helping clients navigate the complexities of IT governance and compliance to achieve greater efficiency, resilience, and security in their IT operations.
In response to the ever-growing seriousness of cyber-attacks, we acknowledge the imperative of staying ahead. Our Framework aims to bolster regulated entities in establishing effective cyber security governance and constructing a resilient infrastructure, complemented by requisite detective and preventive controls. It delineates suitable controls and offers guidance on assessing maturity levels.
Embracing and executing the Framework is a pivotal stride towards ensuring the resilience of Saudi Arabian Banking, Insurance, and Financing Companies sectors against cyber security threats. In crafting the Framework, we have incorporated methodologies for regulated entities to harness technology, envisioning a unified approach for addressing cyber security. This endeavor guarantees that cyber security risks are aptly mitigated across the sectors.
Our company specializes in assisting organizations in Saudi Arabia with compliance to the evolving data management and personal data protection framework. We offer tailored solutions to help businesses navigate the intricacies of data regulations.
Our services encompass comprehensive assessments, strategic guidance, and practical implementation support to ensure adherence to national privacy frameworks and international standards. With a focus on data security, privacy, and regulatory compliance, we empower our clients to safeguard personal data, mitigate risks, and foster trust with their customers and stakeholders. Partner with us to streamline your journey towards compliance and uphold the highest standards of data management in alignment with Saudi Arabia’s evolving regulatory landscape.


Our services encompass robust security monitoring, encryption strategies, and comprehensive security awareness training to fortify defenses against evolving threats. We also offer vendor risk management solutions and facilitate regulatory compliance adherence. With our expertise, organizations can navigate the complex landscape of cybersecurity regulations and standards, ensuring robust protection of critical infrastructure and sensitive data. Trust us to empower your organization with the tools and knowledge needed to achieve and maintain NCA compliance, bolstering cybersecurity resilience in the Kingdom of Saudi Arabia.
Our comprehensive cybersecurity compliance framework assists organizations in Saudi Arabia in meeting the stringent requirements set forth by the National Cybersecurity Authority (NCA). Through a tailored approach, we provide guidance and implementation support across essential cybersecurity controls, including access control, network security, endpoint protection, patch management, and incident response.

Breach and Attack Simulation (BAS) is a proactive cybersecurity framework designed to assess and strengthen an organization’s defenses against cyber threats. By simulating real-world attack scenarios, BAS evaluates the effectiveness of security controls, identifies vulnerabilities, and helps improve incident response processes.
Our company offers expert assistance in implementing BAS, ensuring that our clients can proactively detect and mitigate potential security risks, enhance compliance with industry regulations, and safeguard their valuable data and assets against cyber threats.

.
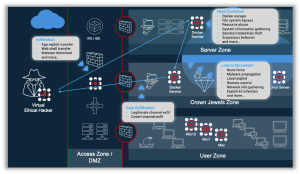
Our approach is widespread on Cyber defense to support your organizations securely open to the world. With 20 plus years of experienced team assessing conventional and zero day threats will surly assist your business to remain secure.
Our Cyber/Infrastructure Security Health Check provide the 360 views of the organization and address key points to mitigate the risk along with bridging the gap on the resilience strategy. Our proved methodology evolves around all business functions to pin-point the exact nature of threats as the starting point in shaping cyber stratagem.


Our process has been designed to identify key areas where operational changes will be required, and to assist the organization in prioritizing efforts for GDPR compliance. Assist in assessing the process to identify, locate, classify and map the flow of GDPR-protected data. Assessing the process of accountability and responsibility in terms of data governance as per GDPR requirements. Focuses on assessing appropriate technical and organizational measures to protect EU residents’ personal data from loss or unauthorized access or disclosure. Identify and assess the requirements of third-party vendors with which you share personal data of EU residents. Assessment of GDPR’s data breach notification and communication requirements. Privacy risks and data protection safeguards of new projects.
GDPR is a major turning point for organizations, and has incentivized them to accelerate their digital transformation efforts as well as build stronger businesses that can thrive and build trust with customers into the next decade. We have established the outline to cater the articles of GDPR and recommend the best outcome based on business understanding and overall dynamics of the operations. Our consultants are well capable and aware of GDPR chapters, articles and recitals. Our unique way to approach data privacy and compliance inline with business with GDPR.


Compliance Wing’s Attack Surface Baseline delivers a comprehensive report that is easy to understand and facilitates informed decisions. The ASB can be tailored to address all or a customized scope of External, Internal and Wireless network testing and assessment. Mobile Application; Web Application; Cloud Services and Virtual infrastructure and Social Engineering Testing and Assessment.
As part of the ASB, Compliance Wing can deploy its tools, a state of the art assessment and remediation tool that allows operations to identify exposed credentials, which may lead to major network breaches.
Penetration Tests have become “lowest bidder” services, offering routine results that don’t increase an organization’s cyber IQ or expose process or technology weaknesses. Compliance Wing’s methodology the Attack Surface Baseline (ASB) assessment, provides our clients with an advanced Penetration Testing and Vulnerability Assessment service beyond what is offered by the rest of the cybersecurity industry.
We differentiate ourselves by addressing the technical, functional and risk-driven aspects of a client’s enterprise while applying knowledge of the client’s business model and processes to place context around vulnerabilities and threat exposure.

Source Code review discovers hidden vulnerabilities, design flaws, and verifies if key security controls are implemented. Compliance Wing uses a combination of scanning tools and manual review to detect insecure coding practices, backdoor, injection flaws, cross site scripting flaws, insecure handling of external resources, weak cryptography etc. Our approach involved both automated and manual detection the hidden peril in SDLC and ensure secure and protected release.

Compliance Wing understands the cognitive aspects of cyber operations. Our professional trainers & curriculum provides the hands-on technical skills require to attain a variety of advanced cyber security qualifications. We instil the knowledge, skills, and abilities necessary for attendees to defeat the adversary. Contact us on info@compliancewing.com for further details.

CW compromise assessment is an evaluation of the organization’s network and systems for artifacts of compromise and it provides proof of the previously unidentified footprint of an attacker or of the existence of Indicators of Attack (IOA) and Indicator of Compromise (IOCs), whether the attacker has been successful or not and whether an attack is ongoing or dormant.

Our qualified DFIR team is geared with all the experience, expertise and tools to respond and restrain the breach affected area for further investigation. Compliance Wing also provide training to in-house staff for Incident Response in order to minimise the impact contain the evidences.
Breaches happen! The right partner can limit the amount of damage done to your network and brand reputation. When you suspect the worst, our Digital Forensics and Incident Response (DFIR) teams are standing by 24x7x365 to answer the call. We treat every organization as our own, working quickly to protect our customers, maintain business continuity, and limit brand damage.
Our DFIR teams are experts with backgrounds in military, intelligence, and law enforcement. We understand the sensitive nature of investigations and focus on fast, thorough, and confidential resolution.


Whether you are a small or large agency, employer, medical or dental practice, CW will satisfy all your essential HIPPA documentation and training requirements. We do Risk Assessment and convert the information to a completed set of documents and safeguard the Protected Health Information (PHI).
Organizations operating in the healthcare industry are continuously under pressure to use resources as efficiently as possible. They must provide innovation in patient care products and services enabled by advances in IT, and do so while maintaining compliance with an increasing burden of privacy and security regulations such as those posed by the Health Insurance Portability and Accountability Act (HIPAA) and Health Information Technology for Economic and Clinical Health (HITECH).


Compliance Wing being a listed company in SWIFT Customer Security Programme has experience and expertise to guide organisations in conforming to the requirements and controls in the SWIFT standards.
“SWIFT does not certify, warrant, endorse or recommend any service provider listed in its directory and SWIFT customers are not required to use providers listed in the directory”
While customers of SWIFT are responsible for protecting their own environments and access to SWIFT, the Customer Security Programme (CSP) has been introduced by SWIFT to support customers and drive industry-wide collaboration in the fight against cyber fraud. The CSP established a common set of security controls known as the Customer Security Controls Framework (CSCF) which is designed to help customers to secure their local environments and support a more secure financial ecosystem.


Compliance Wing threat intelligence as a services are designed to gather data across the global landscape of potential cyber threats, including existing and emerging threats and cyber crime actors, using state-of-the-art tools & methods and, above all is our professional experienced resources who kept on working 24/7 to keep an eye on potential threat and vulnerabilities before they become breach.

Managing cyber security in today’s world is almost indescribably tough. Many business leadership teams don’t feel up to the challenge, or they understand that outside firepower can enhance a security model.
Any Company that is struggling to implement security, comply with industry regulations, and outpace competitors, CW VCISO can help!
![]() Understanding the organization’s strategy and business environment.
Understanding the organization’s strategy and business environment.
![]() Providing threat analysis and strategy updates in real-time.
Providing threat analysis and strategy updates in real-time.
![]() Anticipating future security and compliance challenges
Anticipating future security and compliance challenges
![]() Overseeing mid-level and analyst/engineering teams
Overseeing mid-level and analyst/engineering teams
![]() Discovery, triage, remediation and evaluation of threats
Discovery, triage, remediation and evaluation of threats
Additionally, if your organization is looking to comply with cyber security regulations and standards, our vCISO can help you walkthrough PCI DSS engagement, ISMS ISO27001 assessment, State Bank / Central Bank security audit programs, EU GDPR (General Data Protection Regulation), BCP / DRP engagements, Risk assessments etc. We pride ourselves in adapting to the culture of the client organization. This culture match increases the likelihood of success and reduced client risk. CW vCISO works with your executive and technical teams to get superior results.
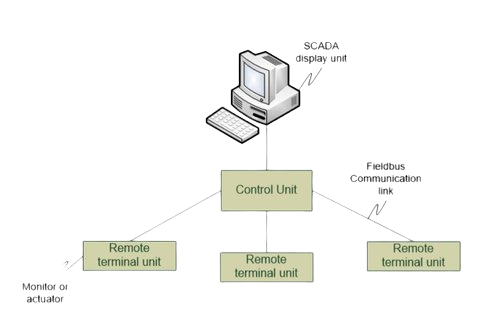
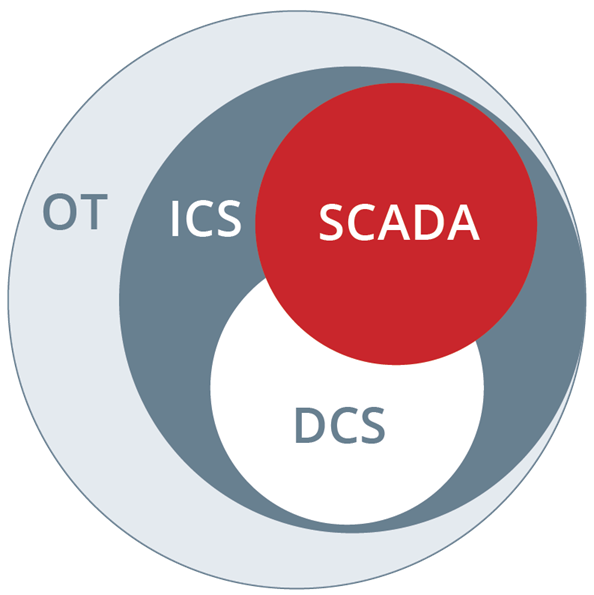
Operational technology (OT) represents systems that are used to monitor and manage the manufacturing equipment or industrial process assets of an organization. OT is a term developed to differentiate it from IT, which represents the information technology assets of an organization. OT is closely related to ICS (industrial control systems) and SCADA (supervisory control and data acquisition systems).
Industrial control systems (ICS) are often managed via a Supervisory Control and Data Acquisition (SCADA) systems that provides a graphical user interface for operators to easily observe the status of a system, receive any alarms indicating out-of-band operation, or to enter system adjustments to manage the process under control. Supervisory Control and Data Acquisition (SCADA) systems display the process under control and provide access to control functions.



Compliance Wing was founded by the team of Information Security experts with years of experience in the field of payment systems as fully independent security assessors.
© 2023 Compliance Wing Private Limited.